Securing Tomorrow with ØKN's Hardware NØDEs

Revolutionizing Security in Networked Computing
In the rapidly evolving world of digital connectivity, security has become a paramount concern. The 0 Knowledge Network has introduced groundbreaking measures to secure access to private networks with a complete stack of components. Within the ØKN Ecøsystem, this includes the foundational levels of physical hardware as detailed in 0KN's comprehensive Hardware Security Documentation. This article delves into the key aspects of 0KN's innovative approach to setting new standards in hardware-based network security.
The 0 Knowledge Network is composed of various "NØDEs" — servers and physical devices that work together to route data securely and anonymously. Physical hardware nodes primary serve two purposes; 1) enhancing decentralized resilience of the network and 2) securing the space between the network and users of the network. The 0KN hardware node unlocks a private decentralized world of utility with incentivized rewards while supporting self-sovereign ownership of data by individuals. The node facilitates metadata-private access to networked applications and helps expand and strengthen the network. With capabilities arising from a Secure Compute Module and custom-designed Operating System, this unit is a crypto-secure Swiss army knife.
Secure Compute Module: The Heart of Hardware Security
At the core of 0 Knowledge Network's hardware device is the Secure Compute Module (SCM4); a component designed to offer unparalleled security in computing applications.
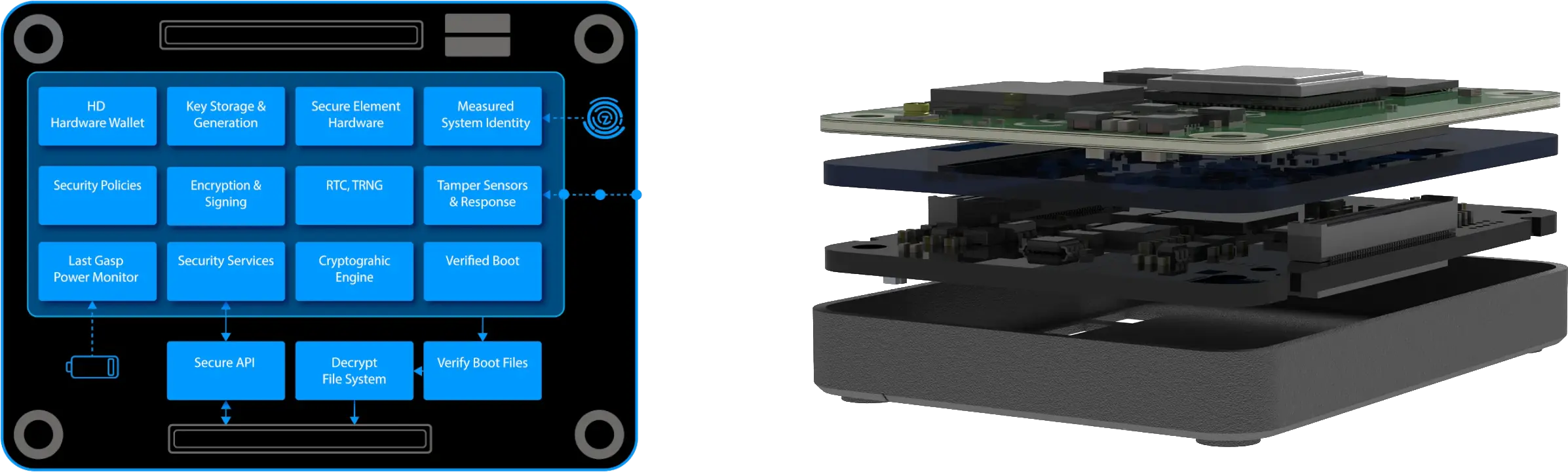
The SCM4 stands out with its array of features including:
- Hardware-Based Security: Incorporating a dedicated secure element, the SCM4 offers superior protection against both physical and remote attacks, surpassing traditional software-only solutions.
- Secure Boot and Firmware: It ensures that only authenticated and signed firmware can be loaded, thereby preventing unauthorized code execution and enhancing system integrity.
- Advanced Encryption Standard (AES): Utilizing AES encryption algorithms, the SCM4 effectively safeguards sensitive data, making it ideal for secure communication and storage.
- Tamper Detection and Response: Equipped with mechanisms to detect and respond to tampering, the SCM4 can protect sensitive information and alert the system in case of physical intrusions.
- Secure Key Management: This feature is crucial for the secure storage and handling of cryptographic keys, maintaining the confidentiality and integrity of sensitive data.
- Integration with Cloud Services: Designed for seamless integration with cloud services, the SCM4 is particularly beneficial for IoT applications requiring secure data transfer and storage.
- Robust Authentication Mechanisms: Supporting strong authentication methods, including mutual TLS authentication, it ensures that only trusted devices can communicate, preventing unauthorized access.
- Compact Form Factor: Its compact size makes it suitable for various devices, allowing developers to incorporate robust security without sacrificing space.
- Ease of Integration and Compliance: The SCM4 is not only easy to integrate into projects but also adheres to industry security standards, ensuring compatibility and interoperability with other secure systems.
ZerØS: A Full Custom Crypto-Secure Operating System

ZerØS, a Linux-based operating system custom-designed for 0KN, is built on the highly secure and optimized New OpSec ØKN+ Linux Kernel, developed by CWD Systems. This integration, along with ARM Trusted Crypto Acceleration features, establishes a robust foundation for zerØS, enhancing both security and performance. This operating system is particularly adept at cryptographic operations, making it an ideal choice for applications where data security is critical. ZerØS parallels mix-networks' defense against external surveillance by rigorously protecting against potential spyware and compromised system components, ensuring the operating system remains a trusted ally rather than an inadvertent adversary. This dual layer of security fortifies users' digital activities against both network-level adversaries and internal system vulnerabilities.
The zerØS desktop UI unlocks a world of open source local-hosted apps with an easy-to-use appstore. It provides access to decentralized mix-net applications and other privacy-focused applications as secured alternatives free from data-tracking intrusions. The zerØS desktop UI gives the user the ability to have a secure privatized micro computer and a private secure router as an access point for local devices. ZerØS desktop environment has a mobile responsive design so you can fully access and use your node at home from your mobile devices.

Securing Tomorrow
The 0 Knowledge Network's approach to hardware security showcases a commitment to providing secure network solutions across a full-stack of potential threat vectors. With the Secure Compute Module (SCM4) and custom-designed zerØS, 0KN is not only addressing current security challenges but also paving the way for future innovations in hardware security. This comprehensive strategy positions the 0 Knowledge Network at the forefront of secure networked computing, offering robust solutions for a wide range of applications where security is of utmost importance.
Read more about features and utility of 0KN hardware within the 0KN Hardware Documentation.
