How Tor Works and Why it Has Weak Anonymity

In a world where online privacy is constantly under threat, tools like Tor promise to keep our digital footprints hidden. But how effective is Tor at truly protecting our anonymity? Delve into the mechanics of Tor, explore its strengths and weaknesses, and discover why its level of anonymity might not be as robust as you think.
Introduction to Tor
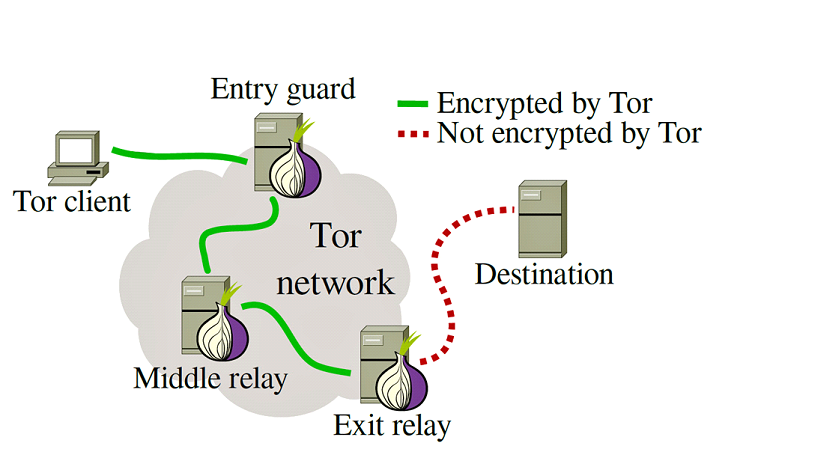
Tor is commonly used like a VPN to help you hide your IP address while accessing common internet services. When using Tor, a client's interactions appear to come from a Tor exit relay node, masking their location. However, Tor offers significantly better privacy than a VPN, with clever features like onion services.
The Tor Threat Model
The Tor threat model operates under the assumption that your Tor client will create Tor circuits whose paths through the network will contain nodes in geographical regions outside the surveillance reach of all their adversaries. However, this model does not account for global passive adversaries (GPA), who can deanonymize a Tor circuit in a few seconds by correlating the timing of stream segments entering guard nodes with those exiting relay nodes. This vulnerability highlights a significant limitation in Tor's ability to achieve strong anonymity, and thus it is considered to have weak anonymity.
Structure of the Tor Network
The Tor network consists of a large set of volunteer-operated relay nodes and a small set of directory authority nodes. Together, the directory authority nodes form the network's public key infrastructure (PKI), responsible for publishing a consensus document at regular intervals. This PKI consensus document includes network connection information and public cryptographic key materials necessary for all nodes to communicate. These documents are cryptographically signed by a known set of keys, which the nodes can verify.
Transport Encryption in Tor
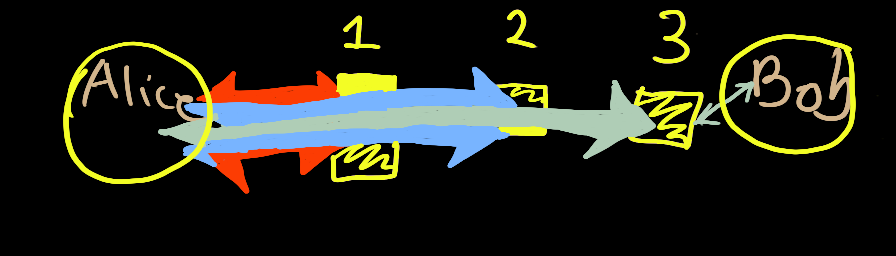
The Tor network uses TLS as the transport encryption protocol between nodes in the network. Clients of the Tor network connect to a guard node using TLS. The client then begins to build a Tor circuit, which consists of multiple nested encrypted two-way streaming connections. This technique, known as onion routing, is sometimes referred to as telescopic onion routing because its nested structure resembles the design of a telescope with nested tubing.
Addressing Anonymity Challenges with 0KN
Addressing the shortcomings of other anonymity tools like Tor, 0KN leverages advanced mix networks to provide superior privacy and ensure application-specific strong anonymity. For a comprehensive understanding of strong versus weak anonymity and how 0KN positions itself in this landscape, refer to our detailed article on Strong vs Weak Anonymity. By embracing advanced privacy solutions, 0KN is committed to providing robust protection for secured communications in an increasingly digital world.
