Security
0KN physical NØDEs are powered by a number of components providing hardware-based security and a custom secured Operating System from the core.
Secure Compute Module
The Secured Compute Module (SCM4) offers several advantages that make it a compelling choice for secure computing applications. Many features - including private key storage, cryptography acceleration, and physical tamper response - have significant relevance within the 0KNetwork both as an end-user device for accessing the network as well as DePIN deployments of devices within Zero-Trust environments. Together, these elements ensure the device, and thus private network connection, remains secured at all times including from potential adversaries with physical access.
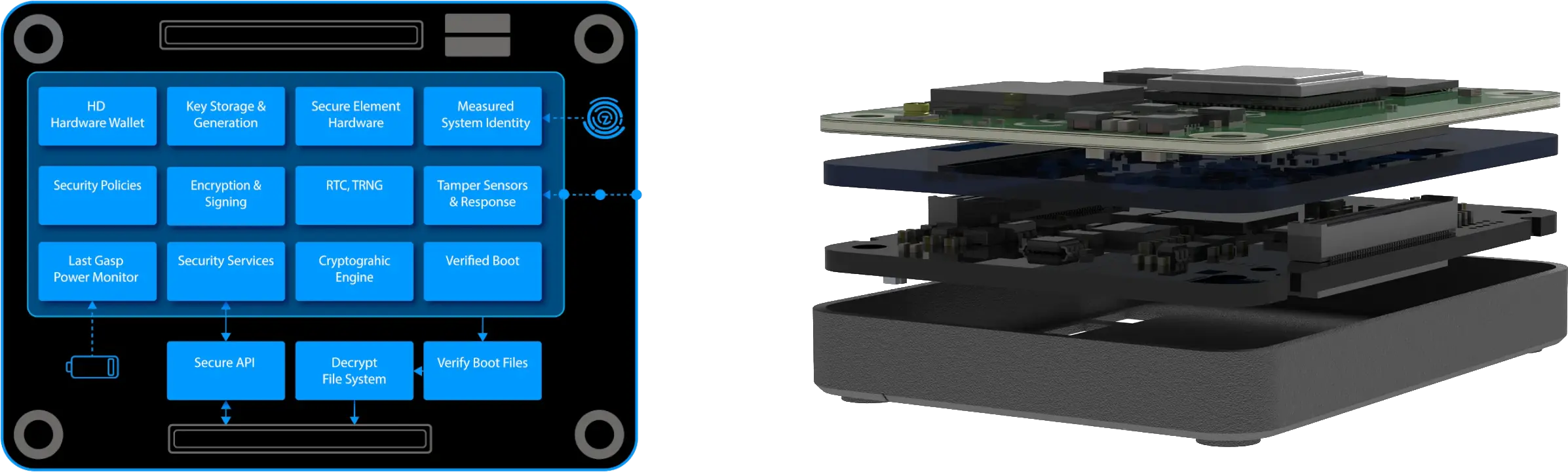
SCM4 Key Advantages
Hardware-Based Security: The SCM4 incorporates robust hardware security features, including a dedicated secure element. This provides a higher level of protection against physical and remote attacks compared to software-only solutions.
Secure Boot and Firmware: The module supports secure boot functionality, ensuring that only authenticated and signed firmware can be loaded, preventing unauthorized code execution. This enhances the integrity of the overall system.
Advanced Encryption Standard (AES): The SCM4 employs AES encryption algorithms to safeguard sensitive data. This symmetric encryption standard is widely recognized for its security and efficiency, making it suitable for various secure communication and storage applications.
Tamper Detection and Response: The module is equipped with tamper detection mechanisms that can sense physical intrusion or tampering attempts. In the event of such incidents, the SCM4 can trigger responses to protect sensitive information and alert the system.
Secure Key Management: The SCM4 includes a secure key management system, which is crucial for securely storing and handling cryptographic keys. Proper key management is essential for maintaining the confidentiality and integrity of sensitive data.
Integration with Cloud Services: The module is designed to seamlessly integrate with cloud services, facilitating secure communication between edge devices and cloud platforms. This is particularly beneficial for IoT (Internet of Things) applications that require secure data transfer and storage in the cloud.
Robust Authentication Mechanisms: SCM4 supports strong authentication mechanisms, including mutual TLS (Transport Layer Security) authentication, ensuring that only trusted devices can communicate with each other. This is essential for preventing unauthorized access to the system.
Compact Form Factor: The compact form factor of the SCM4 makes it suitable for integration into various devices and systems with space constraints. This flexibility allows developers to incorporate robust security features without sacrificing valuable space.
Ease of Integration: The Secured Compute Module provides comprehensive documentation and support, making it easier for developers to integrate it into their projects. This includes software libraries, APIs, and example code to accelerate the development process.
Compliance with Industry Standards: The SCM4 is designed with adherence to industry standards for security, ensuring compatibility and interoperability with other secure systems. Compliance with standards enhances trust and reliability in security-critical applications.
Operating System

ZerOS, a Linux based operating system custom-designed for 0KN, stands out with
its integration of the highly secure and optimized OpSec ØKN+ Linux Kernel,
developed by CWD Systems, along with the added advantage
of ARM Trusted Crypto Acceleration features. This powerful amalgamation
establishes a robust foundation for ZerOS, ensuring not only heightened security
and optimized performance but also leveraging hardware-accelerated cryptographic
capabilities. The ARM Trusted Crypto Acceleration feature enhances the
cryptographic operations within the system, further fortifying ZerOS against
potential threats and ensuring the swift execution of secure communication
protocols. The OpSec ØKN+ Linux Kernel, in conjunction with ARM's trusted
crypto acceleration, places ZerOS at the forefront of operating systems,
offering users a secure, high-performance environment that excels in
cryptographic operations, making it an ideal choice for a wide range of
applications where data security is paramount.
Dedicated Hardware for ZerOS
The ARM v8-based secured hardware appliance, powered by ZerOS and the
OpSec ØKN+ Linux Kernel, represents a cutting-edge solution that seamlessly
integrates robust hardware, advanced kernel technology, and secure compute
modules to achieve optimal performance and guaranteed reliability. This
appliance harnesses the power of ARM v8 architecture, ensuring high efficiency
and responsiveness. ZerOS, with its security-focused design, is complemented by
the OpSec ØKN+ Linux Kernel, offering a fortified operating system foundation.
Leveraging a secure compute module further enhances the device's resistance
against potential threats, providing a secure enclave for critical operations.
The integration of enhanced government-level security features solidifies the
appliance's suitability for sensitive applications, assuring users of stringent
data protection measures. With a commitment to optimal performance, this
hardware appliance is engineered to meet the demands of diverse computing
environments, promising not only unparalleled security but also exceptional
reliability with guaranteed uptime, making it a compelling choice for
mission-critical applications in government and enterprise settings.
Figure 2: ZerOS composition within the Secured Hardware Appliance.